Taking steps to secure your organization’s network is crucial for protecting sensitive information and preventing data breaches.
But maintaining security is challenging in today’s complex IT environments — more companies are turning to hybrid and multi-cloud deployments, and more employees are accessing those networks remotely.
So how can you secure connections to networks and prevent unauthorized access? And how can you enable users to securely access internal applications?
By turning to network solutions like Software-Defined Perimeters (SDP) and Virtual Private Networks (VPN).
In this article, we’ll take a look at what SDPs and VPNs are, how they work, and the main differences between them.
What is SDP?
A Software-Defined Perimeter, or SDP, is a security framework that establishes a perimeter to hide an organization’s internal infrastructure. You can deploy an SDP on-premise or as a service hosted on the cloud.


As the name suggests, SDP establishes a parameter via software instead of hardware. Think of it as an “invisibility cloak,” as resources within the perimeter are completely invisible to outsiders.
SDP works on a “zero trust” basis. Anyone trying to access an organization’s infrastructure is denied secure access by default.
Users can only access resources within an SDP after their identity and device are authenticated. This applies even to those employed by the organization. Unauthorized users won’t be able to access network resources.
SDP also follows “need to know” principles. This means giving users access to only what they need and nothing else. For example, it’s a good idea to restrict access to accounting software to those on the finance team.
Internal users are responsible for more than 40% of data breaches that involved the theft of sensitive information, such as customer data and intellectual property.
The strict access control measures that an SDP deploys make networks more secure against:
- Denial-of-service attacks
- Man in the middle attacks
- Port scanning
- Server vulnerabilities
Any of these attacks can compromise and wreak havoc on an organization’s internal infrastructure.
How does an SDP work?
An SDP is effective for organizations whose IT operations might be spread across public and private systems. It provides IT managers with a means to manage individual users and control what they’re able to access.
Users must verify their identity before they can access resources within an SDP. This is typically done through an identity provider (IdP), a system that manages digital identities. An SDP may also require two-factor authentication (2FA) for extra security.


Even after a user is authenticated, they’re not automatically granted access. An SDP verifies the user’s device to ensure it’s running up-to-date software and free of malware.
An SDP architecture has three main components:
- Client: Users install an SDP client (a piece of software) to the devices they’ll use to access a network. This is typically a desktop computer or mobile device.
- Controller: An SDP controller authenticates users who are attempting to access the network. Once authenticated, this information is passed onto the gateway.
- Gateways: An SDP gateway opens the way for users to access parts of the network they’re authorized to. Network traffic is also encrypted for an extra layer of security.
Each component works in tandem to ensure secure network access and prevent unauthorized users, which goes back to the concept of zero trust.
How does SDP relate to Zero Trust Network Access?
An SDP follows the Zero Trust Network Access, or ZTNA, approach to network security. It assumes that all users and connecting devices cannot be trusted.
This means users must go through the authentication process every time they access network resources, even if they’re already inside the company’s network.
These measures may seem like overkill, but they’re becoming increasingly necessary. More employees work remotely now than ever before, with more than 26 million Americans working remotely at least part of the time according to the U.S. Bureau of Labor Statistics.


If a remote user is accessing a network with a device that has unpatched vulnerabilities, a hacker can exploit those weaknesses and gain access to sensitive information.
Zero Trust Network Access can prevent data breaches, which have long-lasting financial impacts. The average cost of a data breach is $3.86 million.
Deploying an SDP solution is one of the most reliable ways to secure network resources and prevent unauthorized access. Depending on how your company’s infrastructure is set up, you can also consider using a VPN to secure and encrypt traffic to the network.
What is a VPN?
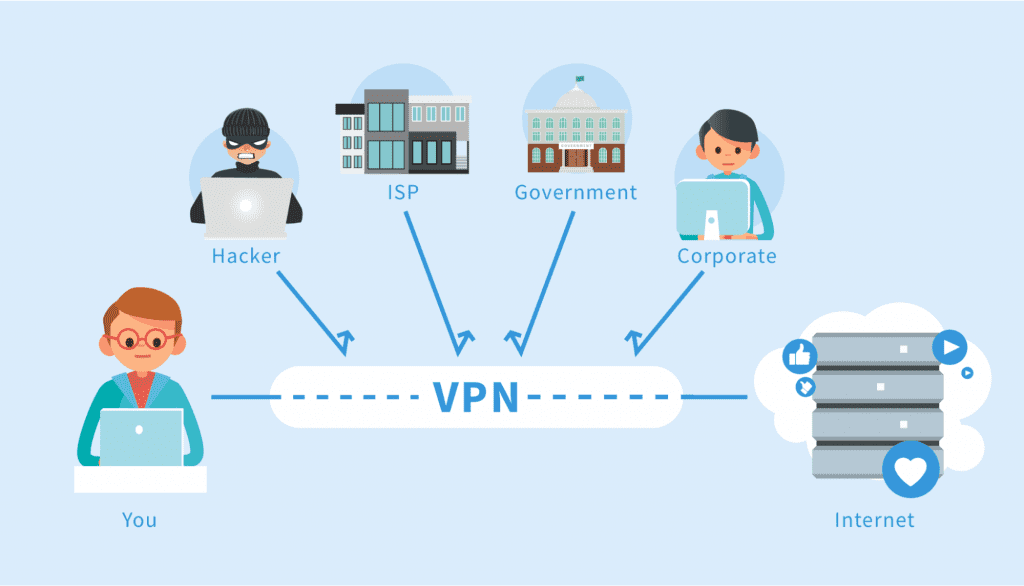
A Virtual Private Network, or VPN, is software that creates an encrypted tunnel between your computer and the internet.
VPN services like ExpressVPN and NordVPN offer native apps for major platforms like Windows, macOS, iOS, Android, and more. This gives you complete privacy and security no matter what device you use to browse the web.
Connecting to a VPN server encrypts internet traffic and hides your IP address — a string of numbers that identifies a device on the network. This prevents hackers, governments, and your internet service provider (ISP) from viewing or tracking your online activities.
Browsing the web using unsecured Wi-Fi networks can also be incredibly risky. Anyone snooping on those connections can steal information like credit card numbers and login credentials.
Despite these risks, 26% of adult online users have logged in to a work email account on a public Wi-Fi network, with 19% having sent a work-related document through one.


Handling sensitive information on unsecured networks puts companies at risk. VPNs provide secure access to internal networks, giving users the flexibility to work outside the office, even if they’re on a public Wi-Fi network.
How does a VPN work?
A VPN works by establishing a secure connection and routing your internet traffic through a private server. This makes it appear as if you’re browsing the web from the server you connect to, which hides your IP address and location.
To establish a secure connection, VPNs rely on protocols — rules that define how your data is encrypted and transmitted over the internet.
VPN providers like ExpressVPN and NordVPN use Advanced Encryption Standard (AES) 256-bit encryption to protect your data.
Even if someone is snooping on your connection, all they would see is scrambled text. It would take a supercomputer millions of years to brute force the encryption key needed to decrypt and unscramble the text.

Businesses may deploy two types of VPNs:
- Remote access VPNs: A remote access VPN creates a secure connection between a company’s network and the devices that connect to it. A remote user can access internal resources even if they’re away from the office.
- Site-to-site VPNs: A site-to-site VPN creates a secure connection between multiple locations. Branch locations can access resources from the corporate network and vice versa.
Remote access VPNs are ideal for companies with employees who require remote access, while site-to-site VPNs are better for organizations with multiple locations. Of course, you’re not limited to one or the other as you can use both at the same time.
What are the differences between SDP and VPN?
Now that you know what an SDP and VPN are and how they work let’s look at some of the main differences between them.
SDP vs. VPN: Security
An SDP is arguably more secure than a VPN. The network perimeter it creates completely conceals an organization’s internal infrastructure. This prevents unauthorized users from accessing resources they’re not supposed to.
Of course, this isn’t to say that VPNs aren’t secure. Premium VPN services like ExpressVPN use strong encryption to protect your internet traffic and keep your data hidden from prying eyes.
But one security risk with VPNs is credential theft. An attacker can access an organization’s network if they have a user’s login credentials or steal their device.
SDP vs. VPN: Authentication
An SDP takes a “zero trust” approach to authentication. The system authenticates each user’s identity and device every time they attempt to access network resources.
A VPN authenticates a user with their username and password, but it doesn’t authenticate their device. This poses security risks if the connecting device is compromised.
SDP vs. VPN: Scalability
Network administrators can deploy an SDP to on-premises, hybrid cloud, and multi-cloud environments. An SDP can quickly scale to accommodate more users and connections as a company expands.
Some VPNs have limitations in terms of how many users can connect at once. But with VPNs like ExpressVPN, you can install a VPN on a router, which then secures all connecting devices.
SDP vs. VPN: Access
An SDP allows for more granular levels of access. This makes it easier for network administrators to provide employees, contractors, and clients with access to specific applications.
In contrast, a VPN may provide users with more access to an organization’s network than necessary, depending on the configuration. To mitigate these risks, network administrators can modify access on an application level.
SDP vs. VPN: Pricing
Deploying an SDP typically costs between $5 to $15 or more per user, making it rather costly depending on the size of your organization.
The best VPNs cost between $10 to $12 per month, but you can bring that number down by subscribing to a long-term plan. You can also configure a VPN on a router and secure traffic for all connected devices.
SDP vs. VPN FAQs
Is using a VPN safe?
Using a VPN is absolutely safe. But you’ll want to use a premium VPN with strong security and privacy features. While there are free VPNs available, some may display ads in your browser or even sell your data to cover overhead costs.
What are the benefits of a VPN?
Premium VPNs like ExpressVPN create a secure tunnel between your computer and the internet. This keeps your online activities private, even if you’re on an unsecured network. Using a VPN can also help you bypass geo-restrictions, avoid censorship when traveling, and even avoid bandwidth throttling that your ISP may impose.
What is SDP used for?
An SDP is used to create a network perimeter around an organization’s infrastructure. This makes it virtually impossible for attackers and unauthorized users to gain access.
Is SDP secure?
An SDP is extremely secure. The system authenticates each user (internal and external) and even checks their devices for vulnerabilities before granting access.
What is zero trust security?
Zero trust security is based on the principle that no one can be trusted. Even the company’s CEO would need to go through the authentication process before they can access network resources.
Is SDP better than VPN?
It depends on what you’re looking for. In some ways, an SDP is better than a VPN because of the extra security features it offers to prevent unauthorized access. But if you’re looking for a simple way to provide remote workers with secure access to internal resources, then a VPN is likely sufficient.
Conclusion
Strong network security is a must. A vulnerable network is more susceptible to data breaches and cyber attacks.
An SDP creates a perimeter around internet-connected infrastructure, which effectively hides it from the outside world. SDP deployments are better suited for large enterprises that have data and applications across multi-cloud environments.
VPNs create encrypted tunnels between a company’s network and connecting devices. Remote users can securely access internal resources even if they’re outside the office. VPNs are ideal for smaller businesses like startups.
If you’re looking for a quality VPN for remote workers to securely access internal resources, then we recommend ExpressVPN.
ExpressVPN consistently ranks as one of the top-rated VPNs on the market, and for good reason — it offers strong encryption and a large network of fast servers. It also doesn’t keep or record any logs about your online activities. You can learn more about this service in our ExpressVPN review.






