Despite its reputation, there are more than a few legitimate uses for torrenting that exist outside of simply downloading pirated content. NordVPN for torrenting offers a convenient and robust protocol for all kinds of decentralized file sharing. Businesses and individuals often need to use peer-to-peer (P2P) file sharing to send and receive large files or download updates for certain software or games.
Unfortunately, though, malicious users can easily access sensitive personal and financial information via the IP addresses of torrenters, thanks to a few vulnerabilities in the protocol.
A reliable way to protect yourself against hackers and scam attacks is by using good VPN software. NordVPN is a fantastic VPN service for those wanting to navigate the world of torrenting safely and securely, thanks to a few key features.
In this article, we’re going to explain everything you need to know about torrenting and then perform a comprehensive review of NordVPN as a torrenting tool. This will include descriptions of the service, its features and privacy measures, and best practices for torrenting safely.
What is torrenting?

Torrenting, also known as peer-to-peer (P2P) file sharing, is essentially a technique where users can distribute and exchange files and data in a decentralized manner.
Rather than downloading an entire file from a single server, you retrieve ‘segments’ of it from various sources, often referred to as ‘seeders.’ These fragments are subsequently assembled by the torrent client upon completion.
BitTorrent serves as the predominant platform for P2P file sharing and proves highly effective for various purposes, which include the following.
Downloading/uploading large files
Because file pieces are downloaded non-sequentially, and in evenly distributed chunks, a download can be halted and resumed at any time during the process without failing, making it particularly suitable for downloading and uploading large files.
Reducing bandwidth demand for hosts
Torrenting is great for the file host. Bandwidth demand is massively reduced because the data is downloaded and uploaded from a swarm of server locations instead of just one.
Increased chance of download success
It’s also advantageous for the recipient because it reduces redundancies and dependencies due to the network’s collaborative nature. There’s no heavy reliance on a single host to ensure successful downloads. Furthermore, with each download, the subsequent shares benefit from increased download speeds. The presence of more seeders also enhances the availability of files.
Torrenting is primarily employed for sharing and acquiring media content such as music, movies, TV shows, as well as computer software, video games, and software updates.
While torrenting itself is entirely legal, downloading copyrighted material through P2P sharing constitutes a legal violation. Despite this, it remains a widely practiced and easily accessible aspect of torrenting.
Why is torrenting dangerous?
Despite its appealing features and advantages, torrenting is not without its share of dangers. When you engage in file sharing or downloading via torrents, you expose yourself to a range of vulnerabilities that can result in significant negative consequences. Your computer may be compromised, your privacy could be laid bare, and your financial data might be susceptible to unauthorized access.
Torrenting presents the following hazards:
Legal Concerns
As mentioned earlier, engaging in the piracy of copyrighted material is against the law and can result in legal consequences, including actions taken by law enforcement agencies or sanctions imposed by your internet service provider (ISP).
Malware Threats
Malware is an encompassing term that encompasses any software designed to harm or disrupt a computer or computer network, which includes viruses and spyware. It can be concealed within files obtained through P2P sharing, leading to disruptions once these files are opened.
Data Exposure
Joining a P2P network exposes your IP address, making it easier for malicious users to track you, access your system, and obtain sensitive personal or financial information from you.


If you are an individual, torrenting without decent protection in the form of a VPN can lead to costly computer repairs, being financially scammed, or legal action being taken against you.
The consequences for a business are much worse, as it’s possible for hackers to gain access and share all the data within an organizational computer network. This includes payroll information, sensitive business plans, and customer data.
How a VPN provider can protect you when torrenting


VPNs fully protect you from the potential dangers of torrenting through a variety of different measures.
Primarily, this is done by masking your actual IP address and replacing it with a VPN server in a remote location. These are shared IP addresses that cannot be traced back to your real location.
The second most important protective measure is encrypting your internet traffic. This way, your ISP will not be able to view your online activities.
There is also a range of other protective measures that VPN services can offer. They are designed to enhance your overall internet security and privacy, even outside of torrenting.
What makes a good VPN for torrenting?
To protect yourself while torrenting and disguise your internet activity effectively, look out for the following features when looking through the various VPN providers out there:
AES-256 encryption
AES-256 encryption is bank-grade cryptographic protection. It protects your data with keys that no known attacker, supercomputer, or cybersecurity agency could ever crack. No one in the modern world has the time or resources to decrypt the key combination successfully.
Additional VPN protocols
VPNs work by protecting your internet traffic in a metaphorical ‘tunnel’ constructed by security protocols. Different providers use different combinations of these protocols, the most common being IKEv2/IPsec and OpenVPN.
DNS leak protection
Domain-name system (DNS) vulnerabilities allow your internet activity to travel through a default DNS, which usually belongs to your ISP. In other words, they will be able to see your activity on torrenting websites. This protection ensures your requests go through an encrypted VPN tunnel. Your ISP will never see them. Some VPNs also offer a kill switch feature, which automatically kills your connection if a DNS leak is detected.
No-logs policy
The last protective measure you might not have considered is whether the VPN provider itself can access your information. Providers with a no-log policy do not collect or store connection timestamps, bandwidth usage, traffic data, IP addresses, or any other data. No-log policies should be verified and approved by independent third-party assessors.
With that said, let’s move on to examining a VPN that might be a great choice for protecting you against the dangers of torrenting — NordVPN.
NordVPN for torrenting: Features and pricing
NordVPN is a virtual private network service provider for Windows, macOS, Linux, iOS, Android, and Android TV.
This VPN provider is notable for its award-winning support team that helps new users navigate the world of VPNs, a very large global server network with over 5,000 servers, and reasonably good connection speeds.
We’re going to be focusing on features that directly relate to torrenting. For a more complete and detailed look at NordVPN, check out our NordVPN review.
NordVPN pricing
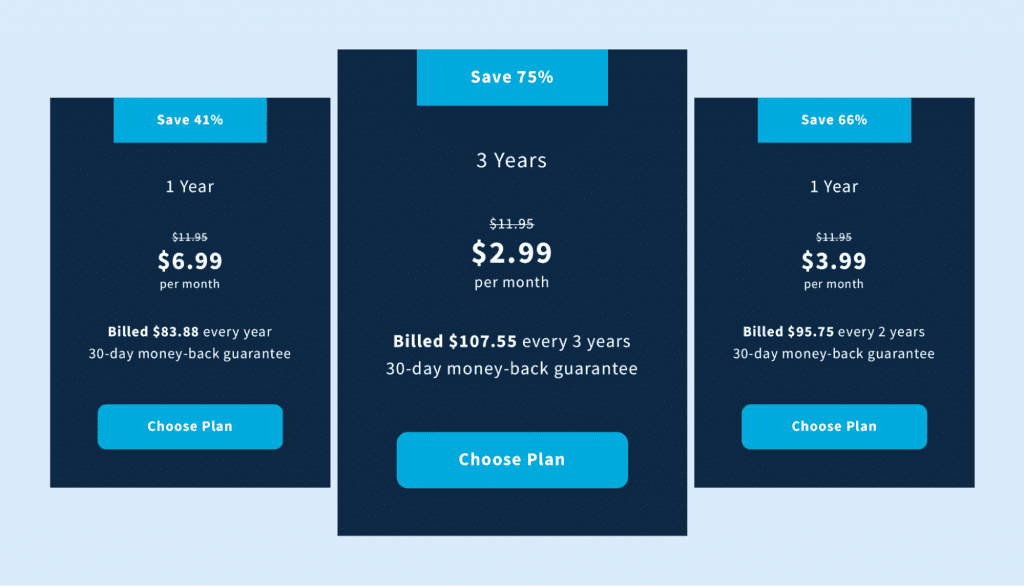
NordVPN offers different pricing options that grant access to the same features but vary by subscription length.
They include:
- One-year subscription: $6.99 per month
- Two-year subscription: $3.99 per month
- Three-year subscription: $2.99 per month

NordVPN for torrenting: Privacy and security
NordVPN is based in Panama. This is relevant because the country has no mandatory data protection laws and is not part of the Five Eyes or 14 Eyes security alliances. This is infinitely better for your privacy and security as a user and torrenter.
This service uses AES-256 grade encryption and the IKEv2/IPsec protocols, as well as OpenVPN and their proprietary NordLynx protocol, which is optimized for connection speed.
This, combined with their independently audited no-log policy and robust DNS leak protection, meets our minimum criteria for security and privacy while torrenting. But there are several NordVPN torrenting features worth highlighting.
VPN Killswitch
If your VPN connection drops for whatever reason, NordVPN offers a killswitch feature. This instantly severs your connection to the internet when and if your connection to the VPN drops.
NordVPN’s killswitch activates at two levels. The system-level killswitch engages a device-wide internet block upon noticing a dropped VPN connection. The app-level killswitch disrupts a particular app you select from connecting to the internet.
This would be great if you use a browser dedicated to torrenting, as you can instruct the killswitch to work only for that browser.
Obfuscated servers
For higher-level security concerns, obfuscated servers are a very useful feature.
These specialty servers disguise that you’re using a VPN, either with an additional layer of encryption or by scrambling your data.
Not only is your internet activity protected with encryption and VPN protocols, but a government or ISP won’t even realize that you’ve taken privacy measures, which in turn won’t arouse suspicion.
CyberSec
As we mentioned, one of the major concerns when it comes to torrenting is unknowingly downloading malware in the form of viruses, spyware, or malicious ads on torrenting websites.
CyberSec is NordVPN’s internet browsing enhancement technology, which works simultaneously as an ad-blocker and suspicious website blocker.
It blocks websites known for hosting malware or phishing scams, as well as protecting you from ‘distributed denial of service’ (DDoS) attacks, even if malware received from torrenting has already infected your computer.
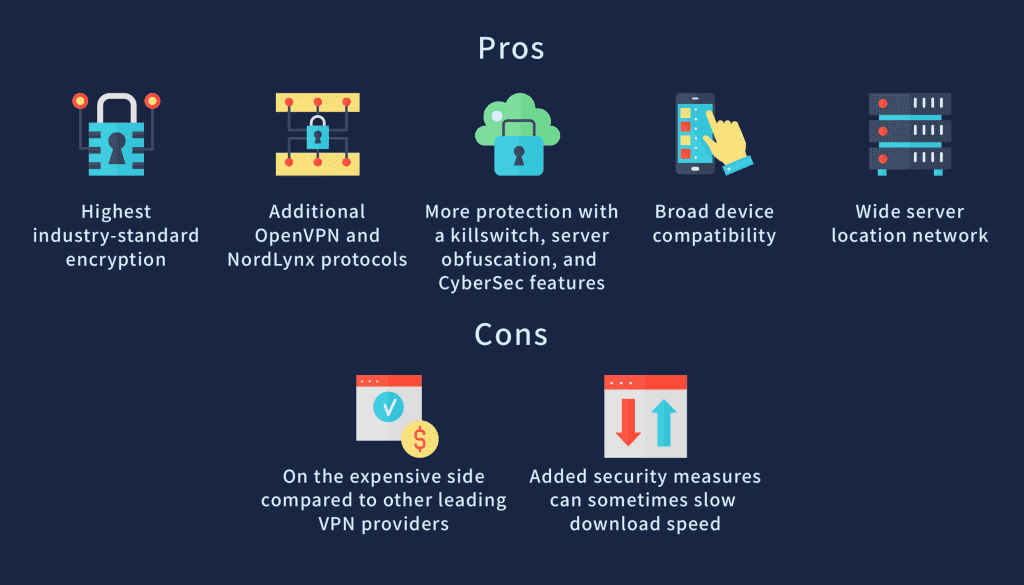
The pros and cons of NordVPN for torrenting
After reviewing the overall service and additional NordVPN features designed for torrenting, we’ve put together a list of the main pros and cons of this platform as a torrenting tool to help you decide whether it is right for you.

Conclusion: NordVPN for torrenting
As you can probably tell, we love NordVPN as torrenting VPN.
NordVPN has a rigorous commitment to protecting users from hackers, government and ISP interference, or any other malicious third parties. It brings security to torrenting through the highest levels of encryption and a host of other features like the killswitch and server obfuscation.
It may not be the fastest VPN, but it’s unrivaled in terms of security and privacy, which makes it ideal for torrenting. You can even take the service on a test run by taking advantage of their 30-day free trial.
However, NordVPN can be a little on the expensive side. If you are happy to make a long-term commitment to the service, it’s slightly more affordable. But if you’re not sure how long you plan on using a VPN service, it might be worth checking out some cheaper alternatives like SurfShark, or providers that offer shorter-term rolling subscriptions like ExpressVPN. For more on NordVPN alternatives, check out our VPN reviews.






